One of the biggest challenges in implementing NIS2 is not technical. It is conceptual.
Many organizations struggle to answer seemingly simple questions:
- what truly belongs to the NIS2 scope
- which elements are critical
- where evidence actually lives
- how governance connects to operations
At the root of this confusion is often one mistake: failing to distinguish between systems and assets.
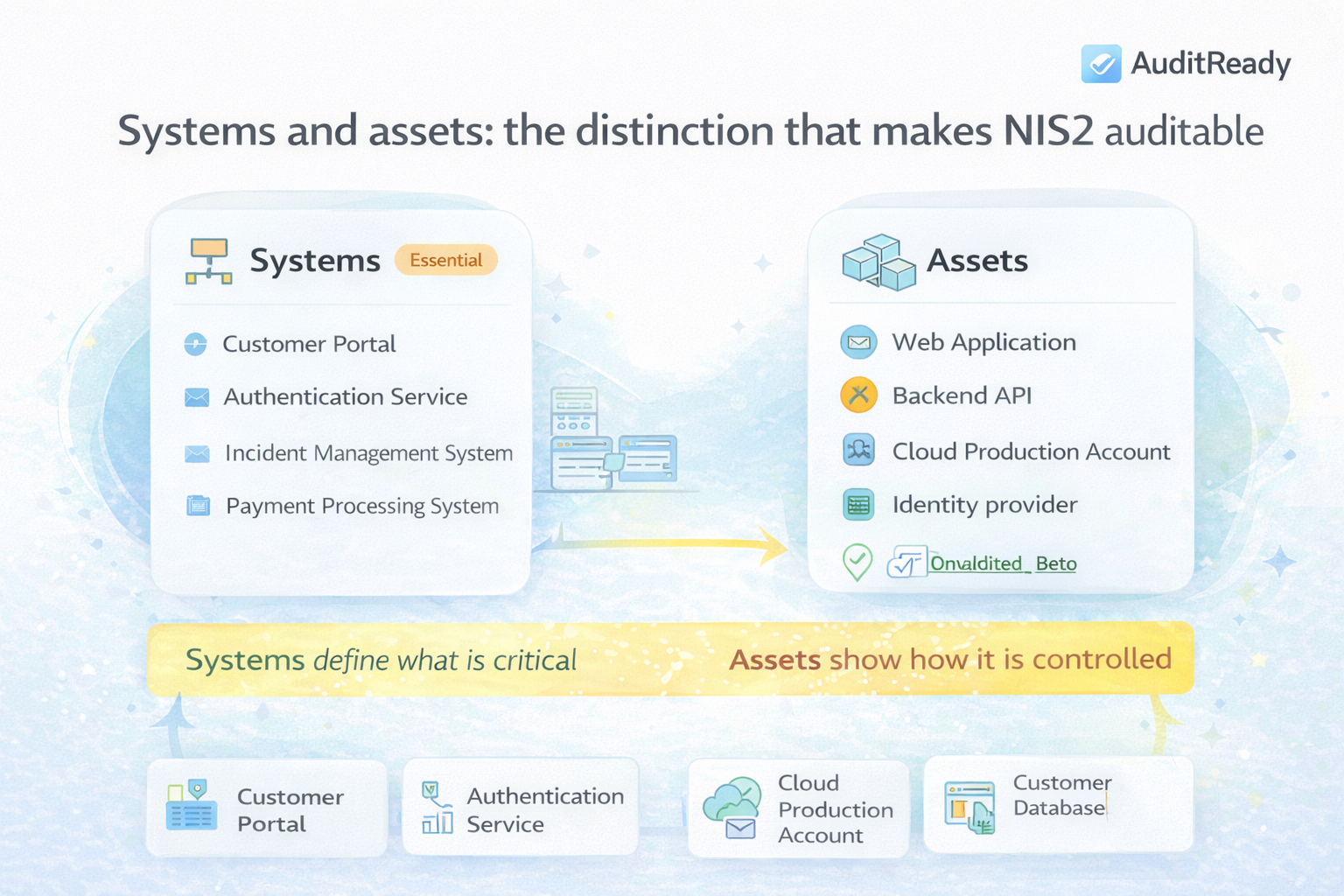
What NIS2 means by “system”
NIS2 focuses on services and functions that support organizational operations. A system is not a server or a tool, but a logical service.
Examples of systems:
- Customer Portal
- Authentication Service
- Incident Management System
- Payment Processing System
A system:
- supports an essential or important service
- has direct impact on continuity and security
- defines what authorities expect to see in scope
NIS2 asks:
“Which systems are critical to delivering your services?”
What assets are
Assets are the concrete components that make a system work:
- applications
- databases
- cloud infrastructure
- identity providers
- monitoring tools
- backups
Assets:
- change more frequently
- are managed by different teams
- are where controls are applied
- are the natural home of evidence
Logs, configurations, test reports, backups: evidence lives on assets, not on systems.
Why this distinction matters for NIS2
NIS2 requires demonstrable control. That control exists on two connected but distinct levels:
- Systems → define what is critical
- Assets → demonstrate how it is controlled
Without this separation:
- scope becomes unclear
- evidence is fragmented
- accountability is blurred
- audits become hard to explain and defend
With a clear distinction:
- scope is readable
- ownership is assignable
- evidence is traceable
- audits become coherent narratives
A practical example
Consider a Customer Portal.
The system is the service as a whole. Assets may include:
- Web application
- Backend API
- Customer database
- Identity provider
- Cloud production account
NIS2 looks at the Customer Portal as a critical system. Your ability to demonstrate compliance depends on:
- which controls apply to the assets
- which evidence exists
- who owns them
- what happens during an incident
Without this mapping, compliance remains abstract.
Inventory as a governance tool, not a CMDB
A common mistake is treating inventory as a technical exercise. NIS2 does not require a full CMDB. It requires understanding and control.
An effective compliance inventory:
- is essential, not exhaustive
- is risk-oriented
- connects systems, assets and suppliers
- supports audits, incidents and reporting
It is a governance tool, not a catalog.
The AuditReady model
AuditReady is built around this distinction:
- systems define the NIS2 scope
- assets host controls and evidence
- audits, incidents and simulations connect the two layers
This model allows organizations to:
- explain compliance clearly
- demonstrate it with real evidence
- sustain it over time without friction
Without a system–asset distinction, NIS2 remains theoretical. With a clear distinction, it becomes auditable.