A document management system (DMS) is not a digital filing cabinet. For regulated organisations, it is a core component of a governance, risk, and compliance strategy—a system of record that provides verifiable evidence of integrity, control, and accountability.
Distinguishing Systems of Record from General Storage
It is a common error to conflate general-purpose cloud storage with a document management system. Platforms like Google Drive or Dropbox are designed for collaboration and file sharing; they were not engineered for the structural demands of regulatory audits. Their function is storage, not the systematic, controlled management of auditable evidence.
For a CISO or compliance professional, this distinction is critical. In a regulated environment, a document's integrity extends beyond its content. It encompasses its entire lifecycle: who accessed it, what was changed, when the action occurred, and under what authority. Standard cloud storage platforms cannot provide this level of non-repudiable proof because they lack the necessary intrinsic controls.
The DMS as a System of Record
A purpose-built DMS is engineered to function as a system of record. It treats documents not as files but as managed assets, each tied to specific controls, policies, and accountabilities. The objective shifts from mere storage to demonstrating how a process was executed under control.
A system of record provides a single, authoritative source of data that is auditable and traceable. For compliance, this means the DMS must guarantee the integrity and lifecycle of the evidence it holds, ensuring it can withstand regulatory scrutiny.
This capability is what allows an organisation to demonstrate compliance, not merely declare it. The system itself enforces the defined governance rules. The relationship between these functions is further detailed in the concepts of governance, risk, and compliance.
Core Principles for Audit Readiness
To be effective in a regulated environment, a DMS must be built on a foundation of control, traceability, and resilience. These principles separate a genuine document management system from a simple storage solution.
- Systematic Control: Access and modification privileges are enforced based on defined roles and responsibilities, not discretionary user permissions.
- Immutable Traceability: Every action performed on a document is recorded in a complete, unalterable log, creating a verifiable audit trail.
- Operational Resilience: The system is architected to support business continuity, functioning reliably during incidents or high-stakes audits.
An auditor's inquiry is not limited to a document's existence. The verification process examines whether the processes surrounding that document are controlled, repeatable, and auditable. A true DMS provides the technical infrastructure to deliver that assurance, transitioning an organisation from administrative record-keeping to provable governance.
Evaluating Core Capabilities for Governance and Control
For a DMS to function as a reliable compliance tool, its controls must be verifiable. These are not features on a checklist; they are the core mechanisms that enable robust, defensible governance. An auditor will not simply ask if policies exist; they will scrutinise the system’s capacity to enforce those policies. Effective governance is built on clear, enforceable rules, and the system itself must be the primary enforcement mechanism.
Enforcing Least Privilege with Role-Based Access Control
Role-Based Access Control (RBAC) is the foundation of a secure evidence management process. Its purpose is to enforce the principle of least privilege, ensuring that individuals can only access the information and functions essential to their defined responsibilities.
For example, a compliance officer may require read-only access to audit evidence across multiple departments but must be prevented from altering or deleting it. Similarly, a system administrator may manage user roles but should be restricted from accessing the sensitive content of the documents themselves. This deliberate separation of duties is a mandatory control in regulated environments. It mitigates risks associated with both human error and insider threats, creating a logical framework that is transparent and verifiable to an auditor. The permission structure becomes a direct implementation of the organisation's governance policies.
Protecting Data Integrity with End-to-End Encryption
Evidence must be protected throughout its lifecycle—both when stored (at rest) and during transmission across networks (in transit). A competent DMS employs strong cryptographic standards, such as AES-256, to render data unreadable to unauthorised parties.
Encryption in transit protects information as it moves between a user's client and the server, preventing interception. Encryption at rest secures the stored files, mitigating risks from physical theft or a breach of the underlying storage infrastructure.
A system that encrypts evidence before it is written to storage provides a higher degree of assurance. This architecture ensures that data is never exposed in an unencrypted state within the production environment—a critical detail for satisfying stringent data protection regulations like GDPR.
This dual-layer protection is a fundamental control. Without it, the system cannot be considered a secure repository for sensitive compliance evidence.
Ensuring Non-Repudiation with Immutable Audit Trails
The immutable audit trail is arguably the most critical capability for audit readiness. It is an unchangeable, append-only log that records every action taken within the system. Each view, upload, modification, export, and permission change is captured with a timestamp and the identity of the responsible user.
The term "immutable" is key. A log that can be altered or deleted has no value as objective evidence. A genuinely immutable audit trail provides non-repudiation—a user cannot reasonably deny performing an action that the system has recorded. This capability is indispensable for forensic investigations and provides auditors with concrete, verifiable proof of all system activity. The audit trail serves as the definitive source of truth, linking every piece of evidence to a clear history of actions and responsibilities. To understand what constitutes robust proof, see our detailed guide on collecting and managing audit evidence.
DMS vs. ECM vs. GRC: Selecting the Appropriate System
In enterprise software, terminology can become ambiguous. Distinguishing between systems like DMS, ECM, and GRC is not a semantic exercise for IT and compliance leaders—it is a functional necessity for building a compliance framework that performs under scrutiny. While all three systems manage information, their purpose and technical depth differ significantly. Selecting the wrong system can result in critical gaps in audit evidence or the adoption of a tool that is overly complex for the required task.
The Scope of a Document Management System (DMS)
A Document Management System (DMS) is designed with a specific function: to protect the integrity of auditable evidence. Its architecture is built to provide definitive answers to an auditor's questions regarding the lifecycle of a document. A DMS acts as the system of record for critical compliance assets—policies, key reports, contracts, and procedural evidence. Every feature, from access control to version history, is engineered to guarantee the authenticity and irrefutable history of each piece of evidence.
The Scope of Enterprise Content Management (ECM)
An Enterprise Content Management (ECM) platform serves a much broader organisational mandate. Its purpose is to manage the flow of unstructured content across an enterprise, including emails, marketing materials, internal wikis, and collaborative project files. While an ECM may include some DMS-like features, its core design prioritizes collaboration and information accessibility over the rigid, evidence-grade controls required for a regulatory audit. Its scope is horizontal, spanning the enterprise, rather than vertical and deep into the integrity of specific compliance artifacts.
An ECM helps an organisation manage its knowledge. A DMS helps an organisation prove its controls. In an audit, this distinction is fundamental.
The Scope of Governance, Risk, and Compliance (GRC)
Governance, Risk, and Compliance (GRC) platforms operate at a higher level of abstraction. A GRC tool is not concerned with the documents themselves but with mapping organisational policies to risks and controls. It functions as a central dashboard for risk registers, compliance tracking against frameworks like ISO 27001 or NIS2, and management of internal audit schedules. A GRC system will indicate that a control is in place but typically relies on linking to external evidence repositories. It lacks the granular, built-in mechanisms to manage the evidence lifecycle directly. The GRC platform is for strategic oversight; the DMS is for execution and proof.
System Scope and Function Comparison DMS vs ECM vs GRC
This table clarifies the primary purpose and operational scope of DMS, ECM, and GRC platforms to help leaders select the appropriate system for their needs.
| System Type | Primary Function | Core Focus | Typical Use Case in Audits |
|---|---|---|---|
| DMS | Securely manage the lifecycle of specific documents. | Integrity, versioning, and non-repudiation of evidence. | Proving a specific policy was approved on a certain date and has not been altered. |
| ECM | Organise and facilitate access to all enterprise content. | Collaboration, knowledge sharing, and workflow automation. | Finding internal project documents related to a new product launch. |
| GRC | Map risks to controls and track compliance status. | High-level oversight, risk management, and reporting. | Showing an auditor the status of all controls mapped to the NIS2 framework. |
These systems are not mutually exclusive; in a mature organisation, they are complementary. The GRC platform manages strategy, the ECM manages general content, and the DMS secures the auditable proof. For any team facing an audit, the latter is non-negotiable.
Selecting a DMS for High-Stakes Regulatory Audits
Selecting a document management system software for a regulated environment is an engineering evaluation, not a general procurement task. The process must prioritize verifiable proof over marketing claims, focusing on system architecture, data integrity, and operational behavior under stress. The primary question is not what a vendor claims the system can do, but what an auditor can independently verify. This requires a detailed examination of the underlying architecture to assess its suitability for high-stakes scrutiny.
The Critical Role of Multi-Tenant Architecture
A foundational requirement for any modern, compliance-focused DMS is a true multi-tenant architecture. In this model, each client's data is logically isolated in its own secure container, often with separate databases and encryption keys. This is not a technical preference but a fundamental control against data co-mingling and unauthorised access. A single-tenant or poorly isolated system introduces indefensible risks, where a breach in one client's environment could compromise others. Verifying that a vendor employs a robust multi-tenant design with strict data segregation is a primary evaluation criterion.
This architectural standard is prevalent in the industry. Cloud-based document management systems are widely adopted in the North American enterprise market because they are built on the secure, multi-tenant models required for modern audits. The cloud deployment segment now accounts for over 67.2% of the global DMS market, a figure driven by the need for scalability and security to meet stringent privacy regulations. Further details are available in the latest DMS market analysis.
Integrity by Design: Immutable Logs and Data Handling
Beyond architecture, the system’s core data handling processes must be scrutinised. An auditor's confidence is predicated on the integrity of the evidence, which begins with how the system records every action. An immutable, append-only log is essential. This means the audit trail cannot be altered or deleted—not even by system administrators. It creates a non-repudiable record of every view, change, and export, providing objective proof of the evidence lifecycle. Any system that permits log modification is fundamentally unfit for compliance purposes.
A vendor’s commitment to engineering discipline is evident in these architectural details. Systems that treat the audit trail as an unchangeable record demonstrate a clear understanding of what constitutes verifiable evidence.
Evaluating Evidence Export Capabilities
During an audit, the ability to export complete, coherent evidence packages is a critical operational capability. This function is more than a simple file download. A compliance-grade DMS must be able to execute asynchronous exports of all relevant documents, their full version histories, and the corresponding audit trail entries. The export process must run in the background without degrading system performance. The output must be an organised, self-contained package—such as a ZIP file or an indexed PDF—that an auditor can navigate without requiring access to the live system. This capability ensures that tight regulatory deadlines can be met with clear, defensible evidence. Understanding the requirements of a comprehensive ISO 9001 audit helps clarify why these export functions are so critical. A system with flexible export options also provides a crucial defense against vendor lock-in, ensuring that an organisation's evidence always remains its own.
A Systems-Based Approach to Implementation and Migration
Implementing or migrating to a new document management system software is an engineering project, not an administrative task. This perspective necessitates a deliberate, phased approach that prioritizes accountability and system integrity. An unstructured implementation process introduces significant compliance risk.
The first step is to establish governance over the project itself. This involves defining the scope, objectives, and responsibilities. An ownership matrix is an effective tool for this, mapping roles such as data owner, system administrator, and compliance approver to specific individuals.
Defining Scope and Mapping Controls
With accountability established, the project proceeds to data classification. Not all documents have the same regulatory weight. The team must categorise information to distinguish between high-stakes compliance evidence, operational records, and general business files. This classification informs the next phase: mapping organisational policies to the new system’s technical controls. For example, a policy requiring quarterly review of access rights must be directly linked to the DMS's RBAC configuration and its reporting capabilities. This exercise frequently reveals discrepancies between policy statements and actual enforcement.
A formal gap assessment is the final verification step before migration begins. This process identifies any misalignments between compliance requirements and the DMS's capabilities. Addressing these gaps before migration prevents the inheritance of old problems and the creation of new ones.
Preserving Integrity During Migration
Data migration is the most complex phase and where evidence integrity is most at risk. The primary challenge is not merely moving files but preserving the continuity of version histories and audit trails. A simple transfer of the latest version of a file destroys its historical context, rendering it useless for audit purposes.
Any migration strategy must therefore address:
- Version History: The complete version history of every document must be transferred and correctly linked within the new system.
- Audit Trail Continuity: The audit log from the old system must be preserved and associated with the migrated documents, even if it cannot be directly imported into the new system’s immutable log.
This ensures the chain of custody for all evidence remains unbroken. The diagram below illustrates the core principles that should guide the selection process, which are also foundational to a successful migration.
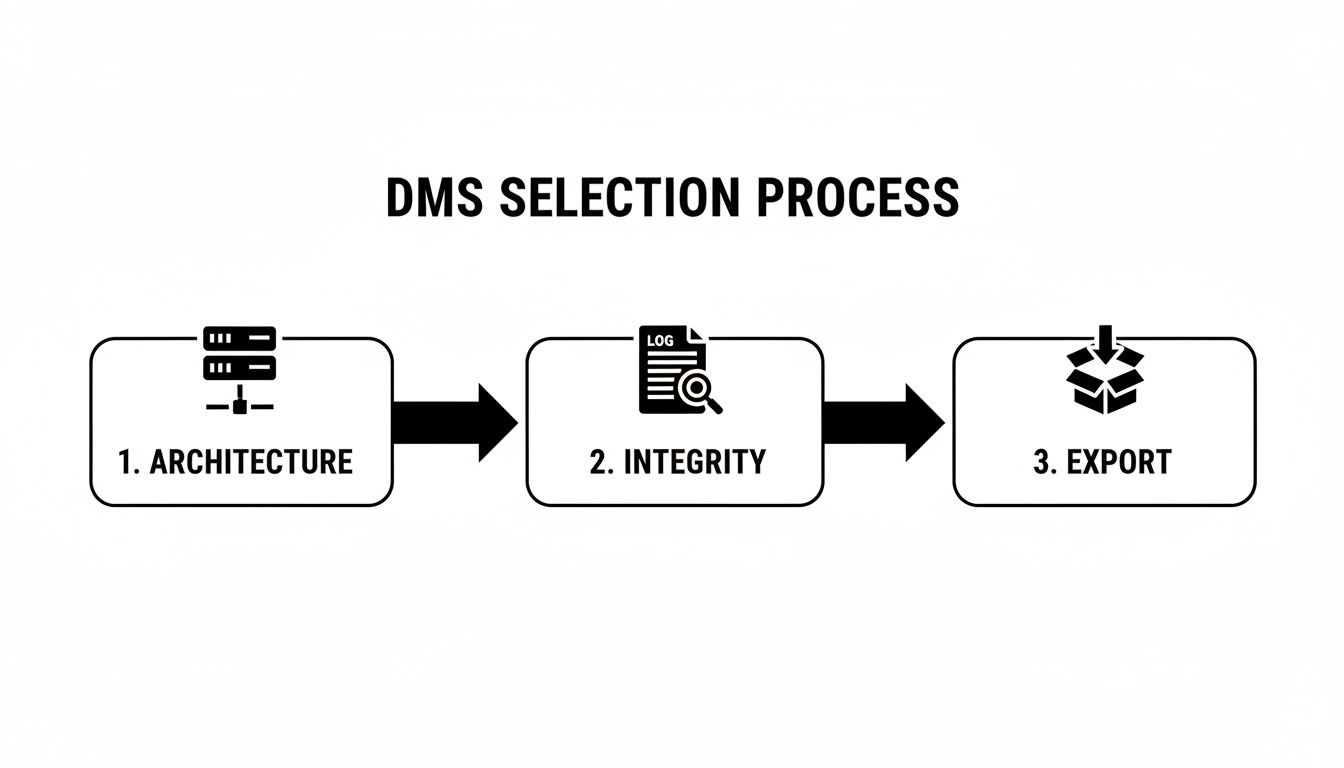
The logical flow is clear: a system's architecture, its mechanisms for data integrity, and its evidence export capabilities are the three pillars of a sound evaluation.
By treating implementation as a rigorous engineering discipline, an organisation ensures the new platform functions as a traceable evidence management framework from its inception. The objective is not just to move files but to transition to a system where controls are demonstrable and accountability is built-in.
A successful migration delivers more than a new tool; it yields a fortified system of record. This methodical approach transforms a high-risk project into a strategic upgrade of the organisation's compliance posture, ensuring the new document management system software strengthens its ability to meet regulatory demands.
Putting Your DMS to the Test: Resilience and Compliance in Practice

The true value of a document management system software is demonstrated not by its feature list, but by its performance under pressure. A DMS transitions from a theoretical control to a practical tool in scenarios such as preparing for a regulatory audit, collecting evidence from third parties, and executing an incident response simulation. In each case, the system provides the structure and traceability that high-stakes scrutiny demands.
Preparing the Audit Day Pack
When a regulator announces an audit, the primary task is to assemble a complete and coherent body of evidence. A purpose-built DMS facilitates the creation of an ‘Audit Day Pack’—a self-contained, exportable package containing all required documents, indices, and logs. This is not a simple data export. A well-designed system enables the generation of a package that includes:
- The Evidence: All requested policies, procedures, and reports, with their complete, unalterable version histories.
- A Clear Index: An organized map linking each piece of evidence to the specific regulatory control it satisfies.
- Immutable Logs: The audit trails proving who accessed the evidence and when.
This exportable package provides regulators with the necessary information in a navigable format, demonstrating organised control without granting access to the live production system. This approach transforms audit preparation from a reactive, high-stress event into a repeatable, managed process.
Managing Third-Party Evidence Securely
Organisations rely on third-party vendors, and auditors will demand evidence of their compliance. However, granting vendors direct access to an internal DMS is an unacceptable security risk. A secure document management system software addresses this challenge through controlled, external-facing portals. For example, a system can allow a compliance manager to send a unique, time-limited upload link to a vendor. The vendor can then submit their evidence into a designated, isolated space within the DMS without requiring an account or gaining visibility into any other part of the system.
This method maintains a strict security boundary while ensuring that third-party evidence is ingested in a controlled manner. Upon upload, these documents become subject to the same versioning, access controls, and audit logging as internal evidence, preserving the chain of custody.
This capability is increasingly important as supply chain security receives greater regulatory focus. The U.S. DMS market in the IT sector is projected to reach USD 5,766.7 million by 2032, driven by such stringent compliance needs. More information can be found in the DMS market trends on fortunebusinessinsights.com.
Executing Incident Response Simulations
Operational resilience frameworks like DORA require not just the existence of an incident response plan, but also its regular testing. These simulations are auditable events, and the evidence collected must withstand scrutiny. During a simulated incident, the DMS serves as the central repository for all related artifacts, including incident logs, communication records, technical reports, and after-action reviews. The system’s version control ensures that a clean, chronological record is maintained as the response effort evolves. The ability to collect, version, and report on this evidence in a structured manner demonstrates a mature incident response capability and proves that defined processes are effective under operational stress.
Frequently Asked Questions
These common questions arise when organisations in regulated sectors evaluate document management systems. The answers focus on systems, evidence, and accountability.
What Is the Difference Between a DMS and Cloud Storage?
This is a critical distinction between a simple storage repository and a controlled system of record. Cloud storage tools like Dropbox or Google Drive are designed for file access and sharing. A document management system software, by contrast, is engineered for governance. It manages documents as auditable assets, tracking their entire lifecycle. A true DMS enforces controls like Role-Based Access Control (RBAC) and captures every action in an immutable audit trail. This is how verifiable proof is generated—the core requirement of regulatory bodies.
How Does a DMS Support Compliance Frameworks Like GDPR or NIS2?
A DMS provides the technical infrastructure to substantiate compliance claims. It does not ensure compliance in isolation, but it provides the tools to prove it.
- GDPR: The system’s access controls (RBAC) and encryption features are direct technical implementations of data protection principles. Immutable logs provide evidence of who accessed personal data, when, and for what purpose, helping to demonstrate lawful processing.
- NIS2: A DMS is used to manage the evidence for incident response plans, security policies, and supply chain risk assessments. It ensures these critical documents are controlled, versioned, and readily available for supervisory authorities.
The system translates written policies into enforceable, verifiable technical controls.
A DMS is not a substitute for a sound governance policy, but it is an essential tool for its execution. It provides the mechanism to enforce rules and the evidence to prove they were followed.
Can a DMS Automate Compliance Tasks?
A DMS automates the enforcement of rules, not the accountability for them. For instance, a system can automatically enforce retention policies by flagging a document for review or archival at the end of its lifecycle. It also automates the logging of every user action, eliminating manual, error-prone record-keeping. However, human oversight remains essential. Individuals are responsible for defining policies, reviewing system outputs, and making final governance decisions. The system is a tool that executes procedures with precision and creates a complete evidence trail; the responsibility rests with the compliance and risk professionals who manage it.
What Should We Prioritise When Migrating to a New DMS?
When migrating to a new document management system software, the primary priority is preserving the chain of custody for all existing evidence. This is not a simple file transfer operation. The complete version history for every document must be migrated, and all historical audit trails must be preserved. Losing this context renders evidence indefensible in an audit. The migration must be treated as a structured engineering project with a clear ownership matrix, ensuring that data integrity is the central focus from initiation to completion.
AuditReady is an operational evidence toolkit built for regulated environments, helping teams prepare for audits under frameworks such as DORA, NIS2, and GDPR. It focuses on clarity, traceability, and execution—not GRC-style scoring. Learn more and get free beta access at https://audit-ready.eu/?lang=en.

