Risk, compliance, and governance are not separate administrative functions; they are integral components of a single, interconnected operational system. Governance establishes the framework and rules of operation. Risk management identifies and assesses potential failures within that framework. Compliance provides the verifiable evidence that the rules are being followed and risks are managed as intended.
Understanding Governance, Risk, and Compliance
To build a resilient organisation capable of withstanding operational stress and regulatory scrutiny, these functions must be approached with an engineering mindset, not as abstract concepts.
When these functions operate in silos, they create critical blind spots. An integrated approach, however, establishes a coherent system for managing operational integrity. This unified structure ensures that every decision is guided by policy, assessed for risk, and verified for compliance.
A Data Centre Analogy
Consider the practical example of operating a secure data centre. For the facility to be both secure and reliable, all three disciplines must work in concert. Treating them as separate functions introduces systemic vulnerabilities.
- Governance provides the operational blueprint and rulebook. It defines access control policies, protocols for hardware installation, and assigns responsibility for system monitoring. It answers the question: "How have we organised ourselves to operate correctly?"
- Risk Management is the systematic threat analysis. This function identifies potential failures, such as power outages, physical security breaches, or HVAC system malfunctions. It asks: "What could realistically go wrong, and what are the corresponding mitigation strategies?"
- Compliance is the mechanism for generating verifiable proof. It involves processes like auditing access logs against the access policy, reviewing maintenance records, and testing backup generators. Its purpose is to answer: "How do we prove our systems operate as designed?"
The Problem with Silos
When these functions are managed by disconnected teams, significant gaps emerge. The risk team might identify a critical vulnerability, but without a clear link to governance, there is no defined owner or process to ensure remediation.
Similarly, the compliance team might focus on validating controls against an outdated policy, completely missing a new risk identified by the security team.
To clarify how these disciplines differ yet depend on each other, it is useful to break them down by their primary role.
Functional Distinctions Between Governance, Risk, and Compliance
This table clarifies the unique role, primary focus, and operational output of each discipline, providing a clear model for their integration.
| Discipline | Primary Function | Core Question It Answers | Key Output |
|---|---|---|---|
| Governance | Establishes direction and authority. | "How should we operate?" | Policies, roles, and decision frameworks. |
| Risk | Identifies and assesses threats and vulnerabilities. | "What could go wrong?" | Risk register, control requirements, and treatment plans. |
| Compliance | Verifies adherence to rules and controls. | "Are we doing what we said we would?" | Audit evidence, attestation reports, and control tests. |
This breakdown illustrates their interdependence. A policy (governance) without a corresponding control test (compliance) is merely a document. A risk (risk management) without a designated owner (governance) is an unmanaged liability.
A siloed approach can create an illusion of security where an organisation is technically compliant yet fundamentally vulnerable. This encourages a culture of checklist adherence rather than a systemic understanding of operational resilience.
True resilience is achieved only when governance, risk, and compliance are treated as interlocking components of a single, unified system.
This integrated view is the foundation of a defensible organisation. It shifts the objective from passing an audit to building an inherently robust and traceable system. Every control can be mapped back to a specific risk and a clear governance mandate, creating an unbroken chain of accountability that provides leadership with a clear view of the organisation's operational health.
Building a Centralized Risk and Governance Framework
To manage risk, compliance, and governance effectively, organisations must dismantle functional silos. It remains common for security teams to focus on technical controls, compliance teams on regulatory checklists, and IT operations on system availability, each operating independently.
This fragmented approach creates systemic flaws, leading to duplicated effort, inconsistent control implementation, and audit evidence scattered across disparate systems.
The core problem with silos is the absence of a unified view of risk. Each team holds a piece of the puzzle but lacks the complete picture. This is particularly dangerous in environments governed by overlapping regulations like DORA, NIS2, and GDPR, where a single control can often satisfy multiple requirements. Without a central structure, mapping these connections becomes a manual and error-prone process.
A centralized approach treats risk, compliance, and governance as one integrated system. It establishes a single source of truth for policies, controls, and evidence, ensuring that all actions are consistent and traceable.
The Systemic Benefits of a Unified Strategy
Centralising these functions is not merely an organisational change; it is a fundamental shift in how risk is managed. The primary benefit is holistic visibility. A unified framework allows leaders to see how a risk in one department might impact another or how a single control failure could trigger multiple compliance breaches.
This structure also drives consistent policy application across the organisation. Instead of different teams interpreting rules independently, a central governance function ensures uniform implementation, which is critical for producing reliable audit evidence.
A centralised model also makes control mapping more efficient. When a new regulation is introduced, its requirements can be mapped against the existing control library, avoiding the need to design new controls from scratch. For more on this structured approach, see our guide to enterprise risk management.
This is the emerging operational standard. Within IT risk and compliance, 91% of organisations now operate with centralised GRC teams—the highest level in six years. This data, available in this compliance benchmark report on hyperproof.io, indicates a clear trend away from siloed models.
Connecting Governance to Executive Oversight
A robust governance framework provides a direct line of sight for executive leadership and the board. The audit committee, for instance, relies on this central system to fulfil its oversight responsibilities. Without a single, coherent view of risk, the board must make decisions based on fragmented and potentially contradictory information.
This need for clear reporting is driving greater demand for cybersecurity literacy at the board level. Directors are now expected to understand not just the financial impact of risk but also its technical and operational underpinnings. A centralised framework provides the concise, reliable data necessary for effective guidance.
A centralized framework transforms governance from a passive reporting function into an active oversight mechanism. It gives leadership the tools to verify that the organisation's stated policies are being executed effectively.
Ultimately, a centralised model enables effective management by creating the conditions for clear accountability, efficient operations, and defensible compliance. It ensures that when an auditor requests evidence, the organisation can provide a complete, coherent, and traceable record demonstrating that its controls are designed correctly and operating as intended.
Engineering Compliance Systems and Controls
Effective risk compliance and governance is an engineering discipline, not a paperwork exercise. The objective is to build robust, verifiable systems that translate abstract policies into tangible, auditable controls. This requires creating a clear, traceable line between stated intent and actual implementation.
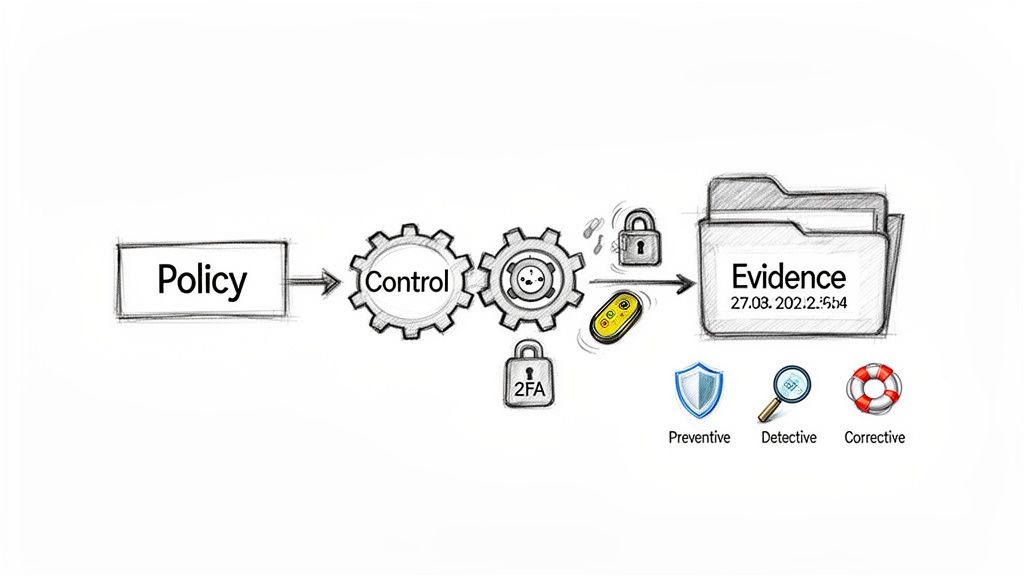
The process begins with distinguishing between policies and controls. A policy defines the 'what' and 'why'—it is the formal statement of intent from governance. A control is the 'how'—the specific mechanism or procedure that implements the policy.
For example, a security policy might state: "Access to production infrastructure must be restricted to authorised personnel via strong authentication." This is the objective. The corresponding control is the mandatory implementation of two-factor authentication (2FA) for all administrative accounts. The control is the direct technical enforcement of the policy.
Designing a Layered Control Environment
A resilient system does not rely on a single control. It employs a layered approach, combining different types of controls to manage risk at various stages. Each control type serves a distinct purpose.
These controls fall into three primary categories:
- Preventive Controls: These are designed to stop an adverse event from occurring. Examples include firewall rules that block unauthorised traffic or Identity and Access Management (IAM) policies that enforce least-privilege access. Their function is proactive defence.
- Detective Controls: These are designed to identify and report when an adverse event has occurred. Intrusion detection systems (IDS), security logging, and file integrity monitoring are common examples. They operate on the assumption that prevention may fail and provide the visibility needed for a response.
- Corrective Controls: These are designed to mitigate the impact of an incident after it has been detected. An automated incident response plan that isolates a compromised system or a data backup and recovery process are corrective controls. Their function is to restore the system to a secure, operational state.
From Control Design to Verifiable Evidence
Designing a control is only the first step. For any audit, you must prove it is operating effectively. Evidence is the immutable proof that a control is a functioning part of your system, not just a statement in a document.
An undocumented control is a rumour. A control without evidence is a belief. Only a control that produces verifiable, consistent evidence can be considered effective in a regulated environment.
This is where the distinction between a tool and a system becomes critical. A vulnerability scanner is a tool. The complete, documented system includes the scheduled scan, the process for triaging its findings, the tickets assigning remediation tasks, and the final verification that vulnerabilities were patched.
The tool automates a task, but the system ensures accountability. Human operators remain responsible for the system's design, execution, and oversight. The evidence it produces—scan reports, triage tickets, patch confirmations—proves the entire system is working as intended. Effective evidence management requires careful organisation, a topic we cover in our overview of document management system software.
Ultimately, engineering compliance means integrating these connections into daily operations. Every policy must have one or more controls enforcing it, and every control must generate tangible evidence of its performance. This creates an unbroken chain from high-level governance objectives to the specific technical configurations that uphold them, forming the foundation of an audit-ready organisation.
Integrating AI Governance into Your Risk Framework
Artificial intelligence introduces governance challenges that traditional risk frameworks were not designed to address. It is a mistake to view an AI model as an autonomous actor. It should be treated as another complex system component that demands rigorous oversight, clear boundaries, and direct human accountability. Integrating AI into operations requires extending existing risk, compliance, and governance structures to cover its unique failure modes.
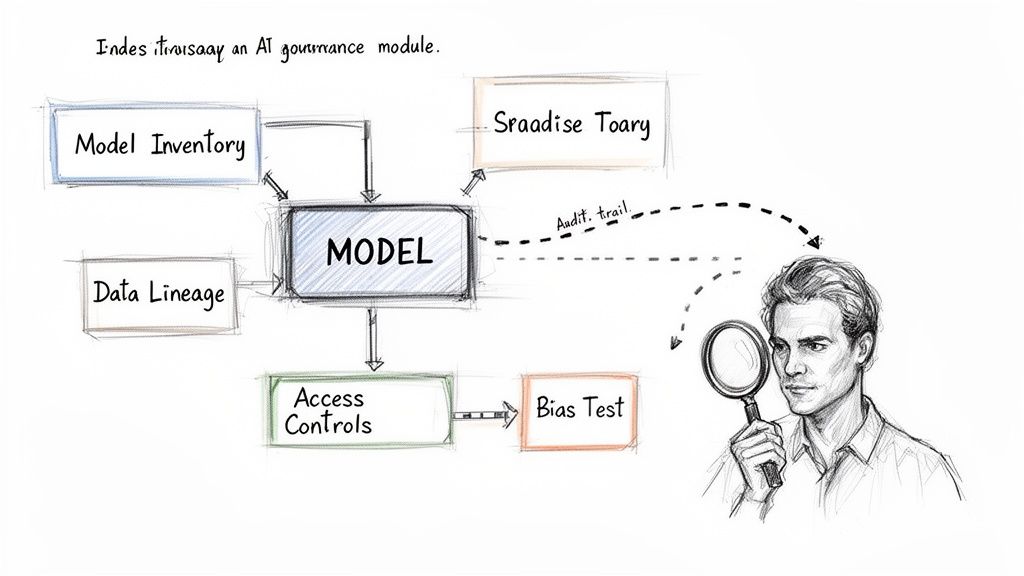
Many significant AI-related risks stem from inadequate engineering and governance practices, not novel threats. These include practical failures like poor dataset versioning, which makes it impossible to trace a model's behaviour, or weak access controls on model training environments. Another common weakness is the inability to produce a coherent audit trail for an AI-driven decision—a basic requirement in any regulated industry.
Traditional governance models are insufficient because they were designed for deterministic systems, where a given input produces a predictable output. Machine learning models are probabilistic and can produce unexpected results. This reality demands a new layer of specialised controls to manage the model lifecycle responsibly.
Establishing New Controls for AI Systems
Effective AI governance requires implementing controls that cover the entire model lifecycle, from data sourcing to deployment and ongoing monitoring. These controls are essential for establishing traceability and accountability in regulated contexts.
Key controls for AI systems include:
- Model Inventories: A central register of all AI models in use, detailing each model's purpose, owner, data sources, and version history. This inventory serves as the single source of truth for all governance and risk assessment activities.
- Bias Testing Protocols: Formal, repeatable procedures to evaluate models for algorithmic bias, both before deployment and during operation. This involves testing with diverse datasets to ensure equitable outcomes and documenting the results as auditable evidence.
- Documented Data Lineage: A complete, traceable record of the data used to train and validate each version of a model. This documentation must include data sources, transformations, and quality checks, allowing an auditor to reconstruct the model's development history.
These controls transform AI from an opaque "black box" into a managed, verifiable component of the technology stack. They provide the evidence needed to demonstrate that the system is operating within defined, acceptable limits.
Connecting AI Governance to Existing Regulations
AI governance does not exist in isolation; it is an extension of existing compliance obligations. When an AI system processes personal data, it falls under the purview of regulations like GDPR. Consequently, requirements for data protection by design, data subject rights, and a lawful basis for processing apply directly to the AI system.
AI is reshaping the IT risk and compliance landscape. According to AI governance findings on knostic.ai, only 7% of organisations have fully embedded AI governance practices, while 93% are already using AI. Furthermore, 97% of AI-related breach victims lacked proper access controls, indicating that enforcement failures, not just policy gaps, are a primary vulnerability.
Treating AI governance as a separate, niche discipline is a strategic error. It is the practical application of core risk management, security, and compliance principles to a new class of technology.
Ultimately, accountability for an AI system's actions rests with the organisation and the individuals who deployed it. By engineering robust governance and control frameworks, you create the auditable evidence needed to prove these powerful tools are being managed responsibly. This proactive approach ensures AI supports organisational goals without introducing unmanageable risk.
The End of Checklists: Navigating the New Regulatory World
The field of risk, compliance, and governance is undergoing a significant transformation. The previous model of periodic, checklist-driven compliance is being superseded by a requirement for continuous, verifiable proof of control effectiveness. This is not an optional shift; it is a direct response to a new generation of regulations designed for a technology-dependent world.
Frameworks such as the Digital Operational Resilience Act (DORA), the NIS2 Directive, and the EU AI Act represent a fundamental change in regulatory expectations. They demand demonstrable operational resilience and rigorous third-party risk management, moving beyond simple compliance statements. These regulations are interconnected elements of a broader push for systemic accountability.
The expectation is now to be 'always audit-ready'. The traditional practice of collecting documents weeks before an audit is no longer merely inefficient—it is an operational and legal liability.
Why Periodic Compliance Fails
This shift is driven by increasing complexity. Regulatory demands are expanding, supply chains are interconnected, and the underlying technology is in constant flux. Attempting to manage this dynamic environment with static, point-in-time assessments leaves dangerous blind spots between audits.
A periodic approach cannot capture the reality of modern IT operations. A control that was effective in January may be misconfigured by March. A third-party vendor that was secure last quarter could introduce a critical vulnerability tomorrow. Regulators understand this and now expect organisational systems and processes to reflect this continuous reality.
Data from PwC’s 2025 Global Compliance Survey validates this trend. 85% of respondents reported that IT compliance has become more complex in the last three years. In response, 91% of companies plan to implement continuous compliance within five years.
From Claims to Systemic Proof
To operate under these new regulations, organisations must design their compliance programs to produce evidence of effectiveness as a natural operational output. This requires a transition to proactive monitoring and automated evidence gathering.
The new regulatory question is not, "Were you compliant on the day of the audit?" but rather, "Can you provide an immutable, time-stamped record proving your controls have been operating effectively every day since the last audit?"
Answering this question is impossible without a systemic approach. It requires controls and processes that generate an auditable, unchangeable trail of evidence. For example, instead of manually sampling firewall rule changes, a continuous system automatically logs every change, correlates it with an approved request, and flags any deviation from policy in near real-time.
This shift necessitates integrating risk, compliance, and governance into daily operations. It involves building a clear line of sight from a regulatory requirement to a specific policy, to the technical control that enforces it, and finally, to the automated evidence that proves its continuous operation. This is the new baseline for building a defensible and resilient organisation.
Implementing a Practical GRC Program
Discussions about risk, compliance, and governance are theoretical; implementation is practical.
An effective GRC program is not a collection of documents but a living system engineered for traceability, accountability, and proof. The goal is to move from periodic, reactive compliance checks to a state of being continuously audit-ready.
The entire structure depends on clear ownership. Ambiguity undermines accountability.
An Ownership Matrix, such as a RACI (Responsible, Accountable, Consulted, Informed) chart, is a foundational step. It maps every control, policy, and process to a specific role, eliminating ambiguity about responsibility. This chart is a governance tool that connects high-level policy to the individuals performing the day-to-day work.
Mastering the Evidence Management Lifecycle
Evidence is the tangible output of a GRC system. A control claim without proof is unsubstantiated.
Evidence management requires a disciplined lifecycle to ensure its authenticity, availability, and audit-readiness. This process transforms compliance claims into verifiable facts.
The key stages include:
- Collection: Systematically gathering proof from controls, such as log files, configuration screenshots, or signed attestations.
- Encryption and Storage: Ensuring all evidence is encrypted at rest (e.g., using AES-256) and stored in a secure, tamper-evident repository.
- Versioning: Maintaining a clear history of evidence over time to demonstrate control effectiveness between audits.
- Secure Sharing: Providing auditors with controlled access to necessary evidence without compromising the entire system.
Proper execution of this lifecycle is fundamental. We cover this in more detail in our guide to effective audit evidence management.
Preparing for Audits as System Verification
An audit should be treated as a system verification, not an inspection. It is an opportunity to demonstrate that the GRC program functions as designed. This mindset replaces last-minute preparation with an organised presentation of pre-existing evidence.
To achieve this, organisations can conduct regular gap assessments to identify control weaknesses before an external audit. Incident response simulations test detective and corrective controls under realistic conditions, generating powerful evidence of resilience.
This represents an evolution in compliance maturity, moving from manual spot-checks toward continuous, automated workflows.
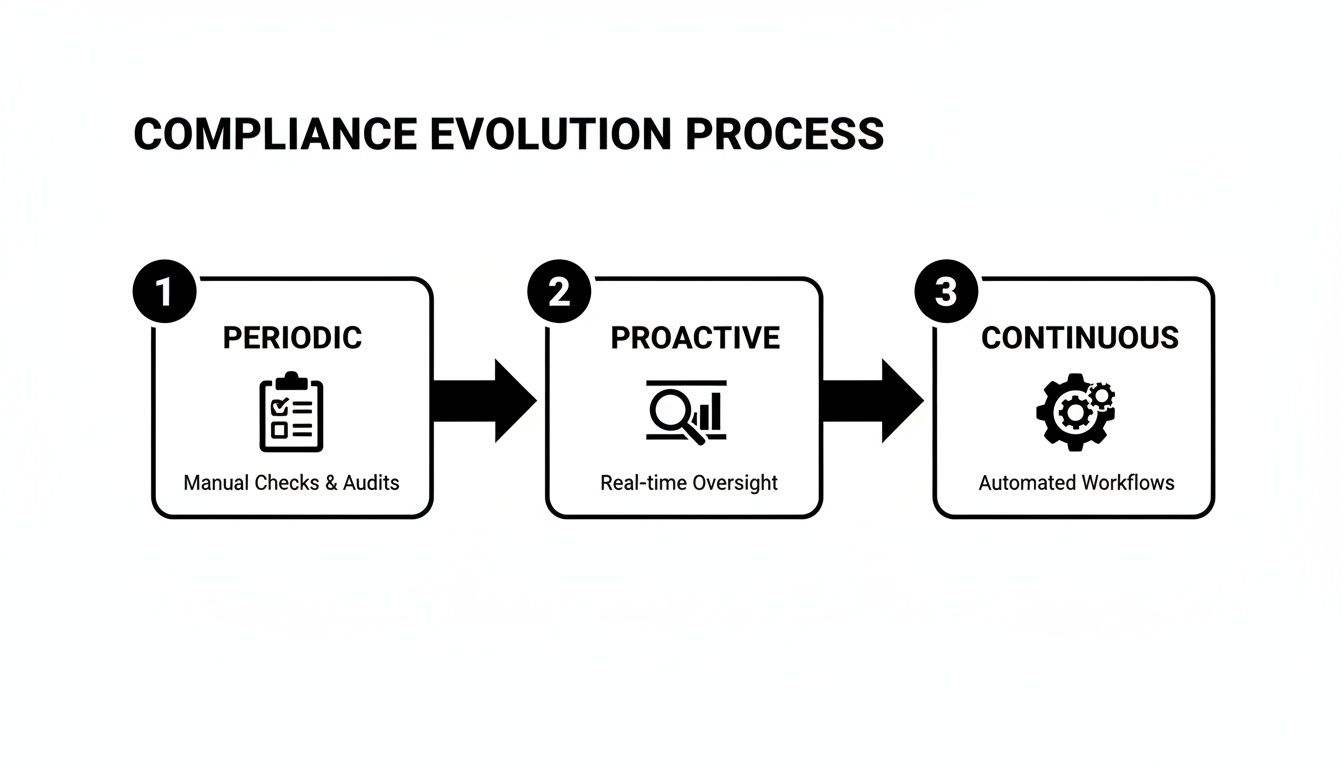
As the diagram illustrates, modern regulations necessitate proactive monitoring and automated evidence collection, rendering older, manual methods insufficient.
The ultimate test of a GRC program is its traceability. An auditor should be able to select any regulatory requirement and trace it to the corresponding policy, the specific controls that enforce it, and the time-stamped evidence proving those controls are effective.
A core practice is the preparation of an audit day pack. This is not a reactive task but a curated, indexed collection of all relevant policies, control descriptions, ownership details, and evidence for a specific audit scope.
Generating this pack demonstrates organisational maturity and allows the audit to focus on verification rather than discovery. This proactive, evidence-first approach is the hallmark of a mature GRC function.
Frequently Asked Questions
What Is the Difference Between GRC and Compliance Software?
Compliance software is typically designed to address a specific set of rules, often in isolation, functioning much like a checklist.
A Governance, Risk, and Compliance (GRC) platform provides an integrated framework. It connects high-level governance objectives and risk management activities to daily compliance tasks. This creates a single, coherent view of how controls support business objectives and avoids the operational silos that compliance-only tools can create. It is a system-level approach to managing organisational integrity.
How Do GRC Tools Support NIS2 and DORA Compliance?
Modern GRC platforms are designed to manage complex, overlapping regulations like NIS2 and DORA. They do not treat these as separate projects.
Instead, they map the specific articles and requirements from both regulations to a single, unified set of internal controls. This allows an organisation to conduct one risk assessment, manage a third-party dependency once, and gather a single piece of evidence that satisfies requirements from both frameworks. The platform creates a traceable link from a control to multiple regulatory demands, which is what auditors require.
Are GRC Tools Only for Heavily Regulated Industries?
While early adoption was driven by sectors like finance and healthcare, GRC frameworks are now used across all industries.
Any organisation facing complex operational risks, managing a network of third-party suppliers, or needing to demonstrate the effectiveness of its cybersecurity controls can benefit. At its core, GRC provides a structure for accountability and evidence-based management—a universal business requirement, not just a regulatory one.
Effective risk compliance and governance is not about maintaining policies on a shelf; it is about building a system for traceability and proof. AuditReady provides the operational toolkit to manage your evidence lifecycle, link controls to policies, and generate audit packs that demonstrate continuous resilience.

